High performance core for payments businesses
API-first approach (400+ REST APIs)
Databases 100% under your control
Isolated cloud infrastructure
Security by design
Flexible CI/CD
PCI DSS compliance (soon)
Tech stack and APIs
Backend
- System core: Java 17
- Frameworks: Spring, Spring Boot, Hibernate ORM
Databases
- Operational DB: PostgreSQL
- Transaction viewer DB: MongoDB
API layer
- 400+ Open API endpoints
- API architecture: REST, gRPC
- Documentation: Swagger
Front-end
- Technologies: VUE.JS, TypeScript
- Version control and CI/CD: GitLab
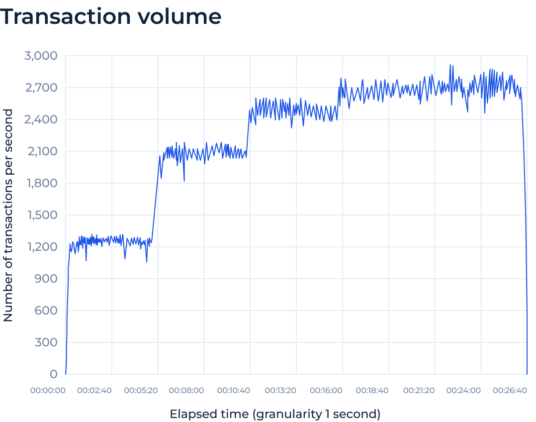
2,700 TPS* workload capacity
SDK.finance transaction processing capacity starts at 2,700 TPS* (business transactions per second) on a basic configuration, which translates to over 230 million daily business transactions to sustain your growth without a hiccup.
See performance testing details
*Internal transactions within the system.
Infrastructure and deployment
SDK.finance Platform is deployment agnostic and can operate effectively regardless of the underlying hardware or cloud infrastructure.
Cloud-based
Available on AWS, Azure, and GCP, allowing for global deployment that adheres to regional compliance and data sovereignty requirements.
On-premises
Deployed in private data centers to cater for specific control, security, or regulatory compliance needs.
Containerized and virtualized
Uses Kubernetes to ensure consistency and reliability across different environments.
Hardware requirements
Here are the minimum requirements of the instance for both Production and Test environments to run the system and ensure its stable performance.
Front end
CPU – 1
RAM – 2 GB
SSD – 40 GB
OS: Ubuntu 22.04 LTS
Software: NGINX 1.18.0
Application server
CPU – 4
RAM – 8 GB
SSD – 160 GB
OS: Ubuntu 22.04 LTS
Software: openJDK 17
Postgres DB
CPU – 4
RAM – 16 GB
SSD – 160 GB
OS: Ubuntu 22.04 LTS
DB: PostgreSQL – 14.4
Transaction Viewer DB
CPU – 2
RAM – 4 GB
SSD – 80 GB
OS: Ubuntu 22.04 LTS
DB: MongoDB – 6.02
Security
We’ve implemented a comprehensive, multi-layered security approach that protects financial information from unauthorized access, cyber threats, and human error.

System architecture security
- ISO 27001 compliance
- TLS encryption and hashing algorithms (SHA-256/512)
- Network & intrusion protection:
- IP filtering
- firewalls
- IDS and WAF

Code quality & security testing
- SonarQube
- OWASP
- unit/integration tests
- static code analysis

Client & staff access
- Multi-factor authentication:
- 2FA and OAuth for both user and staff logins.
- Back-office access controls:
- OTP, HMAC, and role-based access control (RBAC).